Introduction
Palmr supports OpenID Connect (OIDC) authentication, allowing users to sign in using external identity providers such as Google, Zitadel, Auth0, and other OIDC-compliant services. This feature provides seamless single sign-on (SSO) capabilities and centralized user management.
OIDC authentication in Palmr is built using the industry-standard OpenID Connect protocol. The implementation supports automatic user provisioning, and flexible configuration options.
Why use OIDC authentication?
OIDC authentication provides several advantages for organizations and users:
Centralized Authentication: Users can authenticate using their existing organizational credentials without creating separate accounts for Palmr.
Enhanced Security: OIDC provides robust security features including token-based authentication, PKCE flow, and standardized protocols.
Single Sign-On: Users can access Palmr. seamlessly if they're already authenticated with their identity provider.
User Management: Administrators can manage user access centrally through their existing identity provider.
Compliance: OIDC helps meet organizational security and compliance requirements by leveraging existing identity infrastructure.
Prerequisites
Before configuring OIDC authentication, ensure you have:
- Administrative Access: ADMIN privileges in Palmr. to configure OIDC settings
- Identity Provider: An OIDC-compliant identity provider (Google, Zitadel, Auth0, etc.)
- Application Registration: Your Palmr. application registered with your identity provider
- OIDC Credentials: Client ID, Client Secret, and Issuer URL from your identity provider
Supported identity providers
Palmr's OIDC implementation is compatible with any OpenID Connect compliant provider, including as official providers:
Although these are the official providers (internally tested with 100% success), you can connect any OIDC provider by providing your credentials and connection URL. We've developed a practical way to integrate virtually all OIDC providers available in the market. In this documentation, you can consult how to configure each of the official providers, as well as include other providers not listed as official. Just below, you will find instructions on how to access the OIDC provider configuration. For specific details about configuring each provider, select the desired option in the sidebar, in the "OIDC Authentication" section.
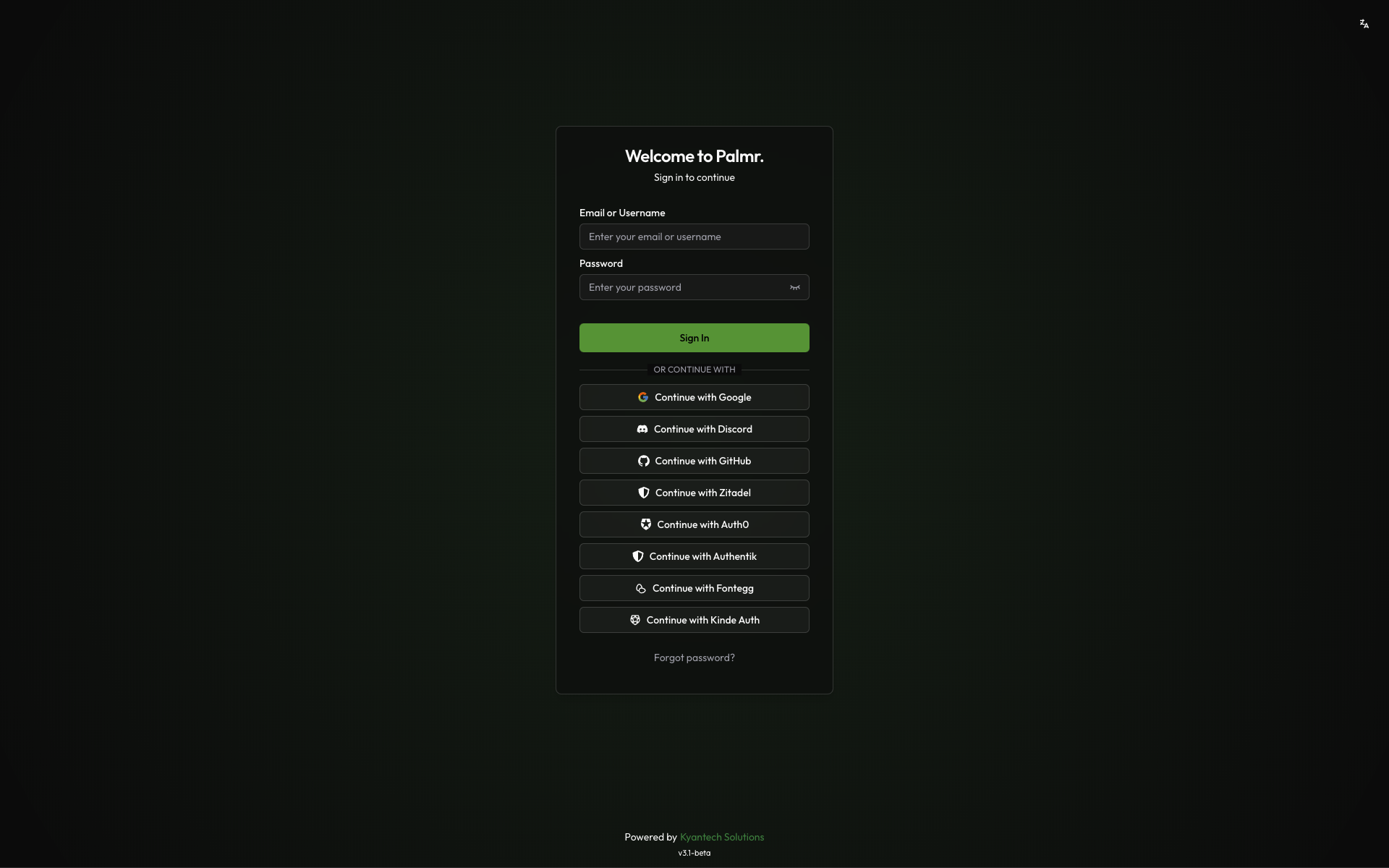
You can use how many providers you want, but we recommend using at least 2 providers to ensure the best user experience.
Configuring OIDC settings
OIDC configuration is managed through Palmr's administrative settings panel, accessible only to users with ADMIN privileges.
Accessing OIDC configuration
To configure OIDC authentication:
- Access Settings: Click on your profile picture in the header and select Settings
- Navigate to Authentication: Find the Authentication Providers configuration section
- Enable OIDC: Toggle the OIDC authentication option to enable it
Note: Consult the documentation of each provider to configure it.
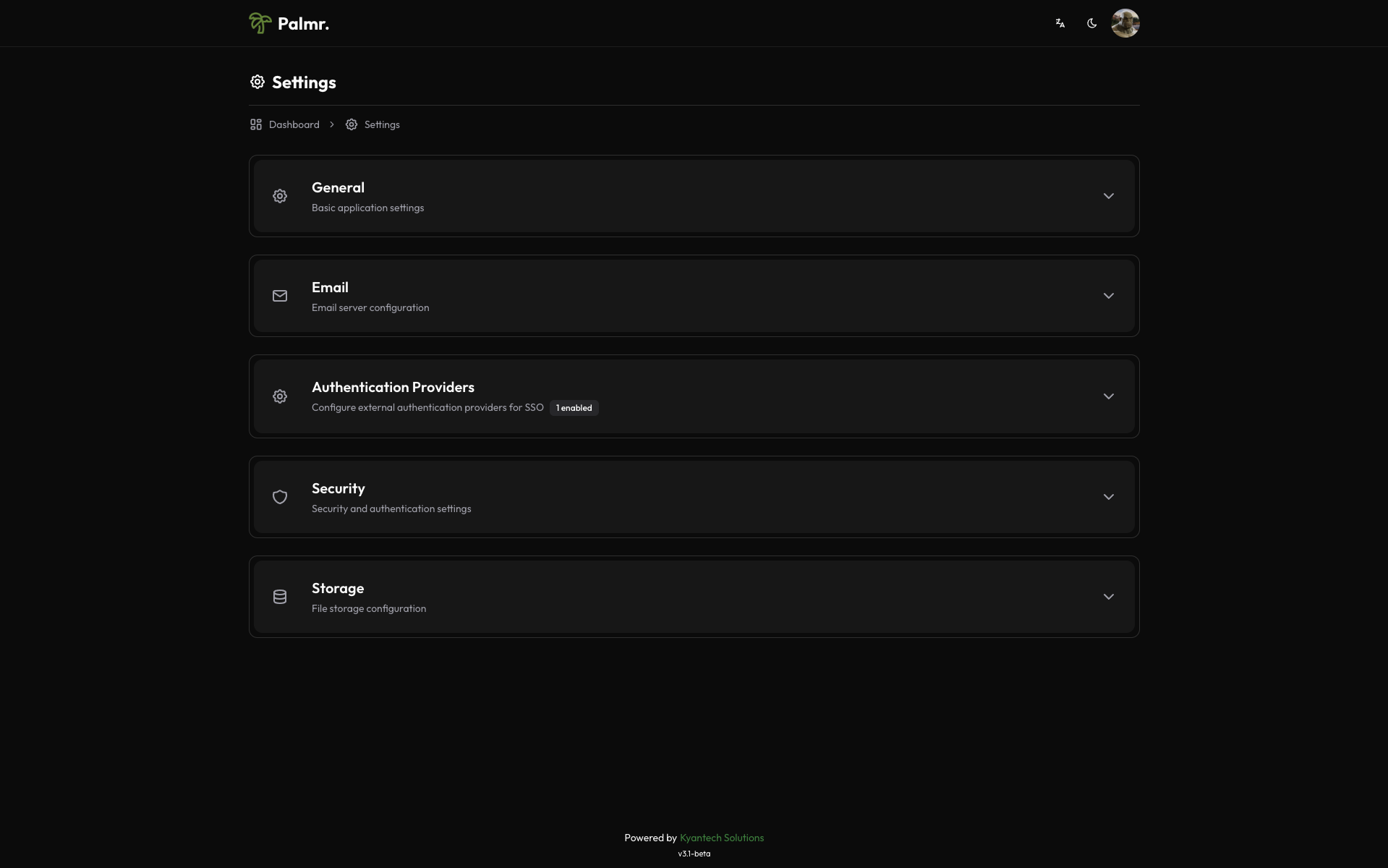
Consult the documentation of each provider to configure it.
Next steps
Select one of the cards below to continue configuring your authentication provider.
Configure authentication using Google OAuth2 services
Discord
Set up Discord OAuth2 for community-based authentication
GitHub
Enable GitHub OAuth for developer-friendly sign-in
Zitadel
Enterprise-grade identity and access management
Auth0
Flexible identity platform with extensive customization
Authentik
Open-source identity provider with modern features
Frontegg
User management platform for B2B applications
Kinde Auth
Developer-first authentication and user management
Pocket ID
Open-source identity provider with OIDC support
Other
Configure any other OIDC-compliant identity provider